Nextcloud includes a server-side encryption application, and when our Nextcloud administrator enables it, all of our Nextcloud data files are automatically encrypted on the server. Encryption is for the entire server, so when it is enabled we can not choose to keep our files unencrypted.
Its main objective is to encrypt files in remote storage services that are connected to your Nextcloud server, such as Dropbox and Google Drive. This is an easy and transparent way to protect our files in remote storage. We can share our remote files through Nextcloud in the usual way, however, we can not share our encrypted files directly from Dropbox, Google Drive or any remote service that is being used, since the encryption keys are stored on our Nextcloud server and they are never exposed to external service providers.
If our Nextcloud server is not connected to any remote storage service, then it is better to use some other form of encryption, such as file level or full disk encryption. Because the keys are stored on our Nextcloud server, our Nextcloud administrator may sniff our files, and if the server is compromised, the intruder can gain access to our files.
Frequently asked questions about file encryption:
The only way to disable encryption is to run the “decrypt all”. Sequence of commands, which decrypts all files and disables encryption.
Is it possible to disable encryption with the recovery key?
Yes, if each user uses the file recovery key, “decrypt all” will be used to decrypt all the files.
Can encryption be disabled without the user’s password?
If we do not have the password of the users or the file recovery key there is no way to decrypt all the files. In addition, executing it when logging in would be dangerous, because it is likely to have waiting times.
Is it planned to move this to the next user login or to a background job?
If we did, we would have to store your login password in the database. This could be seen as a security problem, so none of that is planned.
Is it possible to share in group with the recovery key?
If it refers to adding users to groups and making it work magically, no. This only works with the master key.
Using encryption:
Nextcloud encryption is configured and forgotten, but it has some interesting options that we can use.
When our Nextcloud administrator enables encryption for the first time, we must log out and then log back in to create our encryption keys and encrypt files. When the encryption has been enabled on our Nextcloud server, we will see a yellow sign on the Files page that will warn us to close the session and then log in again.
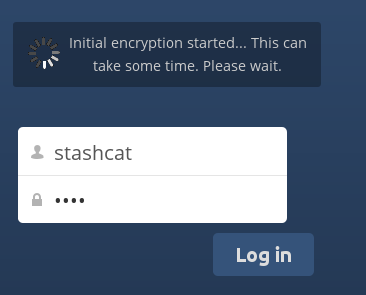
When we return to log in, it will take a few minutes to configure everything, depending on the files we have. The following message will appear: ”Initial encryption started… This can take some time. Please wait”
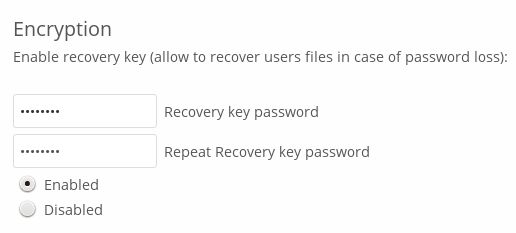
NOTE: We should never lose our Nextcloud password, as we would lose access to our files. To avoid this, we can optionally activate the Recovery key password, explained below.
Files not encrypted:
Only the data in your files are encrypted, and not the file names or folder structures. These files will never be encrypted:
- Old files in the bin.
- Image thumbnails of the Gallery application.
- Previews of the Files application.
- The search index of the full-text search application.
- Data from third-party applications.
There may be other files that are not encrypted; it only ensures that files that are exposed to third-party storage providers are encrypted.
Change private key password:
This option is only available if our administrator has changed his login password, but not his encryption password. This can happen if our Nextcloud provider uses an external user back-end (for example, LDAP) and changed its login password using that back-end configuration.
In this case, we can configure our encryption password to the new login password by providing our old and new login password. The encryption application works only if the login password and the encryption password are identical.